8BASE Ransomware Group Interview:
“We Are Honest and Simple Pentesters”

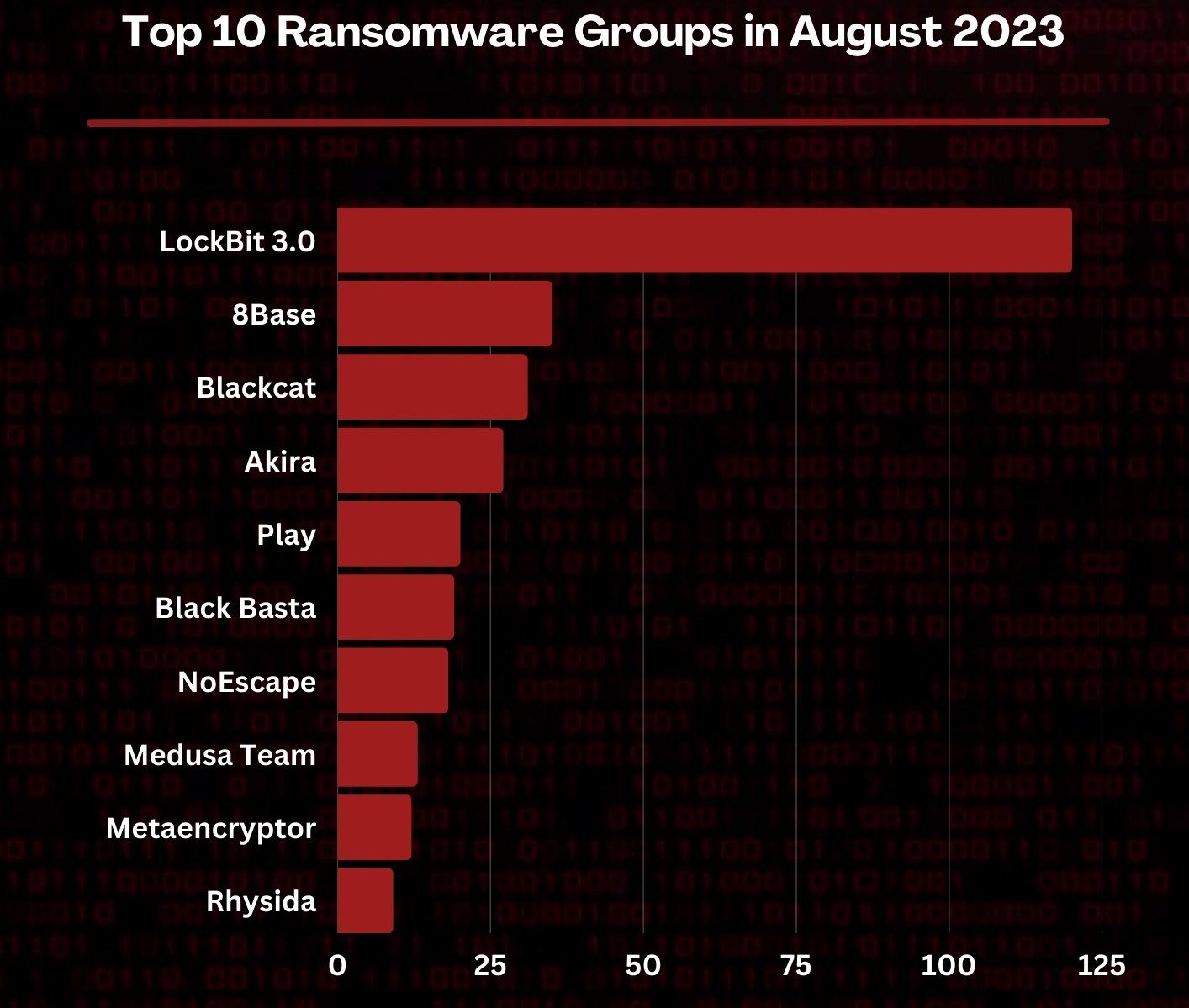
In the early summer months of 2023, the 8BASE ransomware group gained notoriety after a significant increase in its activity. The group today has a lengthy record of breaches, with an average of one ransomware victim every 3.5 days since their launch in spring 2022. Like other modern ransomware gangs, 8BASE employs the increasingly common double extortion tactic of not only encrypting a victim’s data and demanding a ransom for decryption, but also threatening to expose sensitive stolen data if the ransom isn’t paid, thereby intensifying the pressure on the victim. As a VMware Threat Analysis Unit (TAU) report points out, the volume and efficiency of 8BASE’s current operations suggest that this is not a new group but a continuation of an experienced team of malicious actors.
A few weeks ago, I contacted 8BASE and connected with one of their representatives, whom we’ll refer to as Devald, with the aim of learning more about the group’s history and operations. Initially, Devald was approachable and open to a comprehensive interview. However, Devald disappeared mid-interview and now has a Telegram status indicating he was last seen over one month ago (although 8BASE is still active today). Despite our conversation being cut short, Devald seemed to corroborate VMware TAU’s suggestion that 8BASE is a seasoned team of ransomware actors. Devald also provided additional insights into the group’s background and activities.
I initially asked Devald about 8BASE’s composition and what roles members have. Devald revealed: “We have a very large team, it has about 20-25 people of different nationalities and beliefs. Each has [their] own task, one person is looking for vulnerable networks, several people are collecting data, there are several negotiators, as well as [our] own developers. We are all people of the world and the Internet, so we have no racial quotas and prejudices. We value professionalism.”

Regarding primary motives, Devald explained: “Of course, it’s the financial side, we want to earn as much money as possible and retire. This is the most important thing in our work.” After asking what percentage of victims end up paying their demanded ransom, Devald was hesitant and said: “Unfortunately, this information will remain undisclosed, but let’s just say that smart directors pay, and you will never know about them on our leak sites. Their protection subsequently becomes very serious because we provide a very detailed report and instructions on how to improve their security system online.”
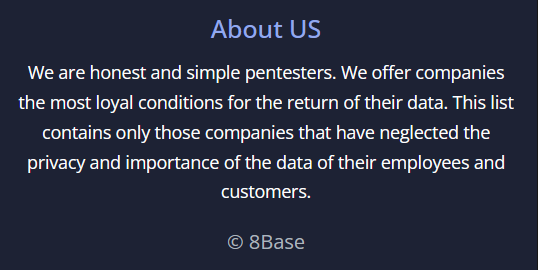
This last part – allegedly providing a company with a report on how to improve their security posture – ties into the branding on 8BASE’s .onion site: “We are honest and simple pentesters. We offer companies the most loyal conditions for the return of their data.” I asked Devald how 8BASE justifies the contradiction between this self-description and their illegal extortion activities, and he replied: “Look, we are honest. We openly find vulnerabilities in networks and help fix them. Of course, we do it in our own way, you need to look at the answer of the primary motives question to understand why [for profit]. We do not justify anything; it is as written.”
After being pressed on the illegality and unethical nature of leaking personally identifiable information of innocent individuals, Devald portrayed 8BASE as good guys simply raising awareness about data protection: “You understand, we are trying to show that this can be avoided, but the heads of companies only think about their wallets. We also think about their wallets. Companies must either engage in competent organization of the security system or pay money to keep customer and employee data hidden from the eyes of other people.”
Discussing red lines that the group will never cross, Devald claimed: “We do not undertake work on organizations that are engaged in critical things; it is unsafe for the health and life of people. Therefore, we are aimed only at organizations that are potentially willing to pay. After all, we give many chances; we try to find a common language with each client and come to the right and profitable solution for us and for the client.”
But what exactly is unsafe “for the health and life of people?” 8BASE has previously dumped patient data from several healthcare facilities, including IDs, phone numbers, and addresses. One could argue that such a combination alone is unsafe “for the health and life of people.”
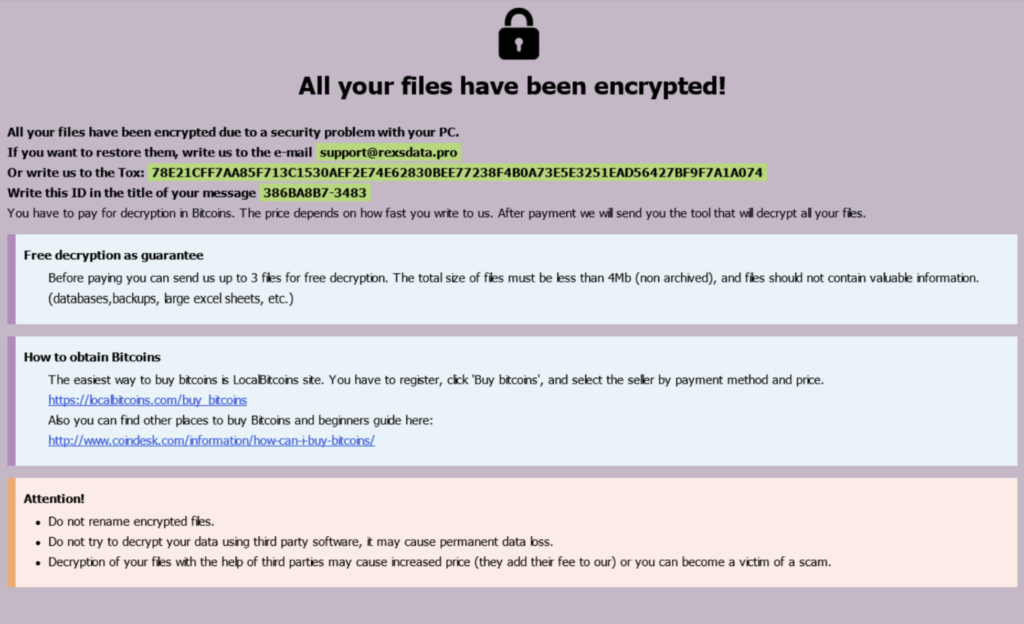
We shifted gears and briefly discussed the group’s work from a technical perspective. Devald explained that the group gains initial access to a target’s network primarily through phishing, adding: “It’s always different, mostly, of course, social engineering. We try to get inside the company through vulnerable employees, then we use different methods… The weakest link is always the person in the company.” Devald shared additional information: “For each company, we develop our own unique software that, based on information about the target computer, can increase privileges. For each client, we make new software, and it is always unique. Decryption files are subject to 100% after payment, if none of the system administrators decided that he was a hero and did not try to recover the files on his own.”
Regarding antivirus evasion, Devald said: “Antiviruses are not a problem at the moment, because when setting them up, the system administrator usually makes a lot of mistakes. We also have a few tricks that, in 98% of cases, help to easily bypass antivirus solutions.” Devald also touched on 8BASE’s anti-forensic techniques to hinder incident response efforts, telling me: “We work with a number of people from cybersecurity who help mislead investigators. It is very convenient and not expensive.”
I asked Devald if 8BASE mostly develop in-house tools or if they prefer to use third-party ransomware as a service (RaaS). As VMware TAU reported, analysis of an 8BASE sample determined the group was using “Phobos ransomware version 2.9.1 with SmokeLoader for initial obfuscation on ingress, unpacking, and loading of the ransomware.” Devald explained: “We develop our own and also use purchased software. Sometimes it’s easier to pay a certain amount of money and get a quality product than to invent your own. In our community, people are professionals in their field, and everyone is ready to cooperate with each other in order to earn.”
Using Doc2Vec, an unsupervised machine learning algorithm that can be used to identify similarities in documents, VMware TAU discovered that 8BASE’s ransom note had a 99% match with RansomHouse’s ransom note (RansomHouse is a cybercrime group that debuted in late 2021 and is still active in 2023). Also, the language used on both groups’ victim-shaming sites is almost identical. I asked Devald about these similarities, and he candidly stated: “Well, you know, it’s not new when specialists from one group move to another and so on. And someone shares their experience and best practices.”
I also asked Devald how 8BASE handles law enforcement agencies and cyber threat intelligence firms tracking their cryptocurrency transfers. In a preposterous claim, Devald said: “Well, we clearly understand the need to share, and therefore many cybersecurity and law enforcement agencies receive some compensation so that the traces do not lead anywhere.” Devald did not reply to my follow-up request for clarification on sending “compensation” to law enforcement.
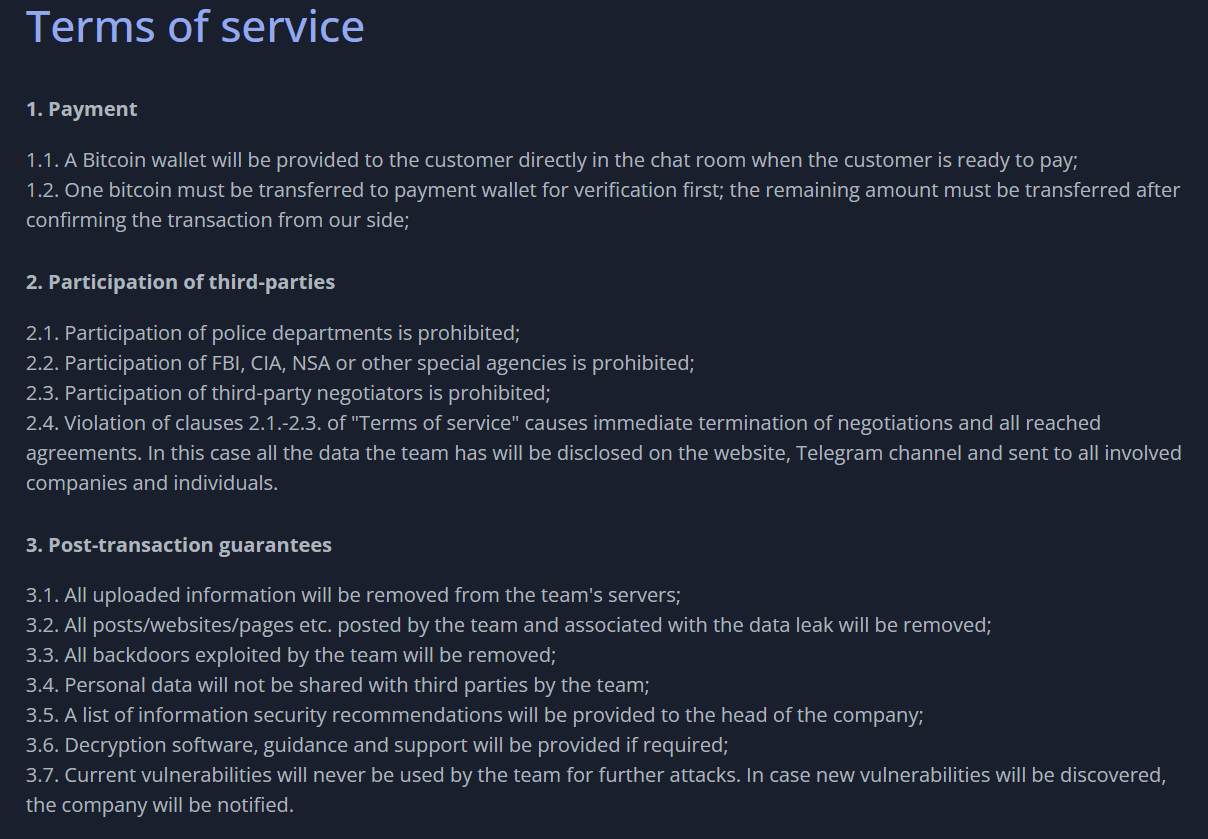
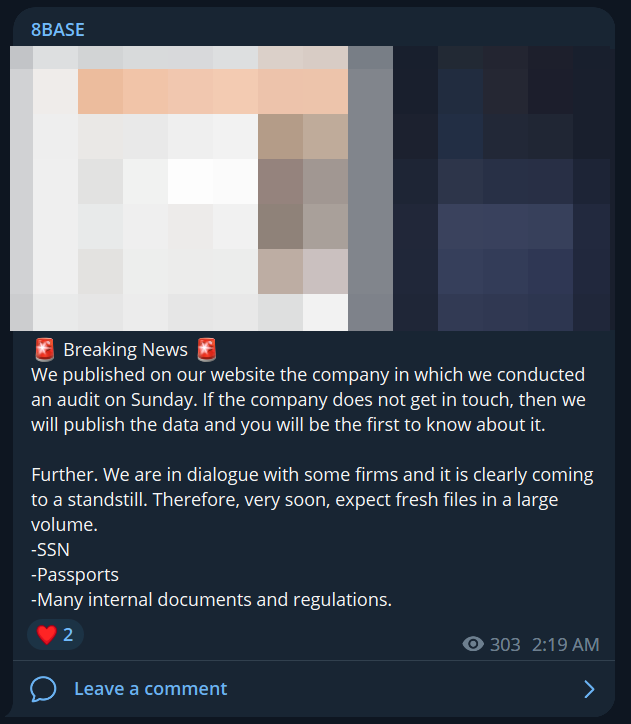
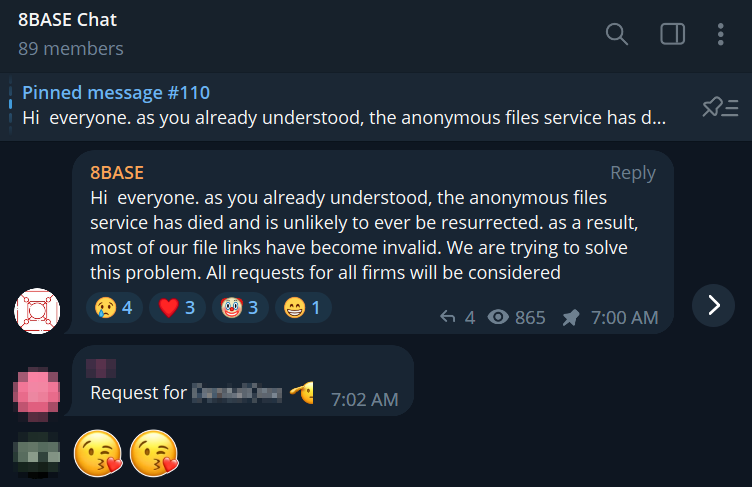
8BASE recently faced a setback with the permanent closure of AnonFiles, a popular website in the cybercrime community for the past two years. AnonFiles shut down due to the overwhelming amount of abuse on their platform, despite their efforts to implement automated content moderation. In the past, the group regularly shared links to ZIP files hosted on AnonFiles, which contained sensitive data obtained through ransomware attacks.
On August 17, 2023, in an 8BASE Telegram group chat separate from their main Telegram leak channel, the group offered to re-upload data previously hosted on AnonFiles based on custom requests. Just two minutes after announcing this, the group received their first request from a user asking for a re-upload of data from an Australian dental care facility. It is worth noting that 8BASE has not solely relied on AnonFiles but has previously used Mega, GoFile.io, and Files.dp.ua to host and share data.
The last thing Devald shared me with was a general recommendation for organizations to protect against ransomware attacks: “Train every employee, from a cleaning lady to a company director, about what the Internet is. This will help. Thank you.”
